The tech industry has been predicting the end of passwords/passkeys for years. Those guarantees have been little more than hollow promises for years. There were as many usability and security issues with password replacements as there were solutions, such as pushes, OAUTH single-sign-ons, and trusted platform modules. We’re finally on the verge of a password replacement that works.
Passkeys are a new alternative. Passkeys generally refer to various techniques for storing and authenticating information in hardware, an idea that has been around for more than a decade. What’s new is that Microsoft, Apple, Google, and a group of other companies have united around a single passkey standard shepherded by the FIDO Alliance. Passkeys are not only easier for most people to use than passwords; they are also entirely immune to credential phishing, credential stuffing, and other account takeover assaults.
PayPal customers can now log in using FIDO-based passkeys, joining Kayak, eBay, Best Buy, CardPointers, and WordPress. Microsoft, Apple, and Google have all enabled passkeys in recent months. Spotty passkey support. iOS and macOS passkeys work on Windows, but not vice versa. All of it should be resolved soon.
Other places won’t get access until “early 2023.”
Read also: A New Tap-to-Pay Service for Mobile Devices in Nigeria is Now Available
What exactly are passkeys?
Passkeys operate similarly to FIDO authenticators that let us utilize phones, laptops, PCs, and security keys for multi-factor authentication. Passkeys are undetectable and connect with Face ID, Windows Now, or other biometric scanners. The only method to extract cryptographic secrets from authenticators is to dismantle or jailbreak them. Even if a threat was able to figure out the cryptographic secret, they would still need to provide a fingerprint, facial scan, or PIN. if the token doesn’t have biometric capabilities. Also, hardware tokens use FIDO’s Cross-Device Authentication flow, which uses Bluetooth Low Energy to ensure the device doing the authentication is close to the device trying to log in.

Until now, FIDO-based security keys were mostly used for MFA, which stands for “multi-factor authentication.” This type of security requires someone to show more than just the right password. FIDO’s extra factors are usually something the user has, like a smartphone or computer with a hardware token, and something the user has, like a fingerprint, facial scan, or other biometric, that never leaves the device.
So far, attacks against FIDO-compliant MFA have been in short supply. For instance, an advanced credential phishing campaign recently breached Twilio and other top-tier security companies for one reason: Unlike the other targets, Cloudflare used FIDO-compliant hardware tokens that could not be tricked by phishing. The victims who were breached all relied on weaker forms of MFA. But while hardware tokens can use a password and one or more other ways to prove who you are, passkeys don’t need a password at all.
Passkeys, on the other hand, combine multiple ways to prove who you are, like the user’s phone, laptop, face scan, or fingerprint, into a single package. The OS of the device takes care of passkeys. End-to-end encryption can also be used to sync them with the user’s other devices using a cloud service from Apple, Microsoft, Google, or another provider. This is done at the user’s choice.
An enrolled device may automatically transfer a passkey across an encrypted tunnel to another enrolled device attempting to sign in to one of the user’s sites or applications. The user logs in with the same fingerprint, on-device password, or PIN that they use to unlock their device. This method replaces the username and password and makes it easier for the user.
Users no longer need to enrol each device for each service, as they did with FIDO, “Andrew Shikiar, FIDO’s CMO, remarked. “By securely syncing the private key across an OS cloud, a user only has to sign up for a service once and is already signed up on all of their other devices. This makes it easier for end users to use and gives service providers the ability to get rid of passwords for account recovery and re-enrollment.
Setting up a Passkey
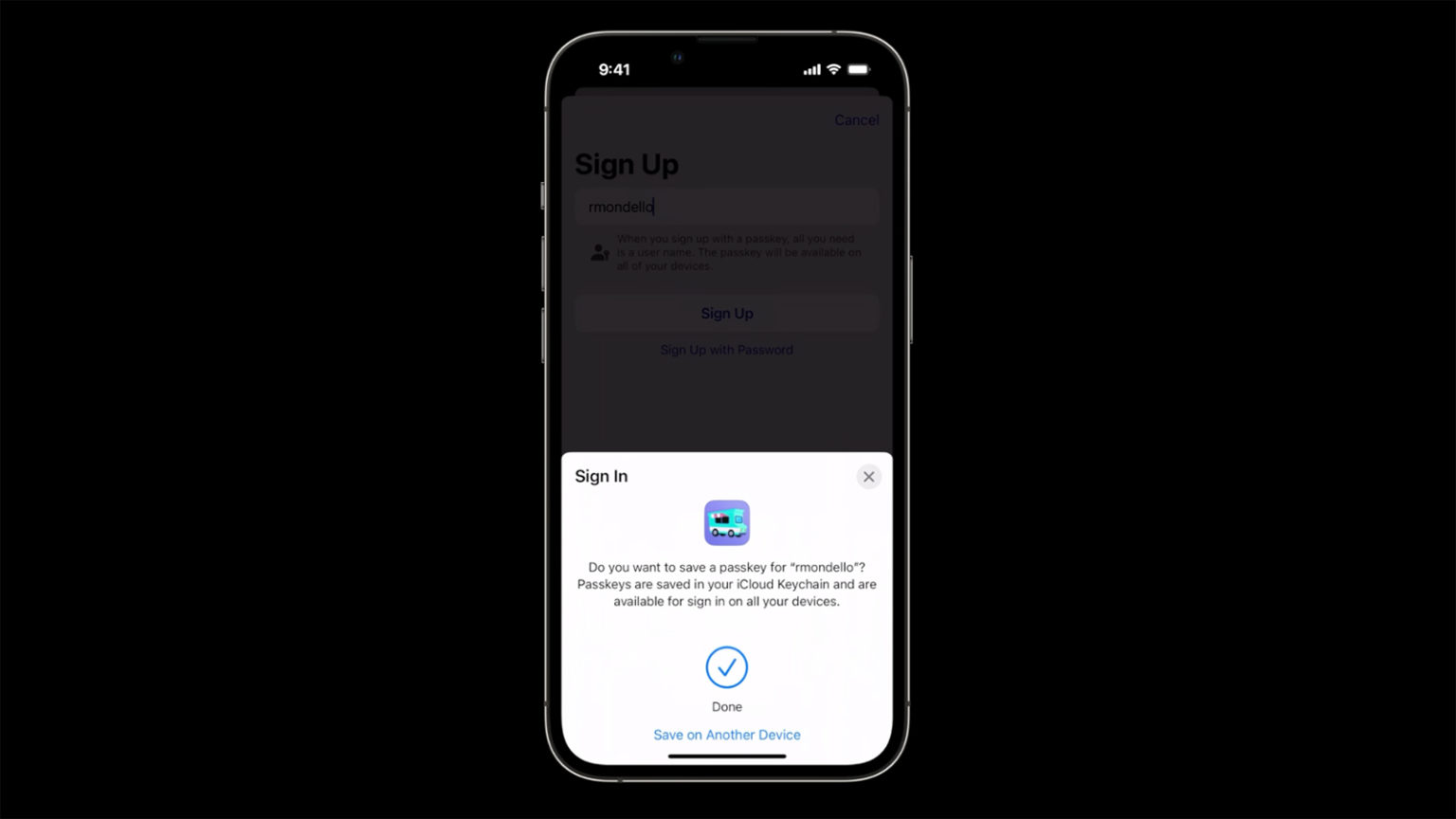
To create a new passkey with a compatible app or website, you enter a username and authenticate with Touch ID or Face ID. Your passkey is made and sent to the iCloud keychain. That means you can use your passkey to log in from another Apple device running iOS 16, iPad OS 16, or macOS Ventura. Signing in uses the autofill system you already know, and you don’t have to do anything else besides confirm your username and login. To put it another way, you tap and sign in. It only takes one step, so you don’t need extra security measures like two-factor authentication.
You can also look at the user settings of an existing account on any website that lets you, but it’s not always called a passkey. For example, we tested the functionality on eBay’s website and found a setting called fingerprint sign-in tucked away in the Sign-in and Security section of the Account Settings. Other websites that work with this one will be similar. Also, note that the eBay app doesn’t currently support passkeys. This is for the website only.
How to log in on a PC or Android phone.
Since your passkeys are on iCloud Keychain, you may be wondering how to login on a PC or Android phone. Things become difficult, but not too much. Your phone scans a QR code and then connects to the target device through Bluetooth. After authentication, you’re in.
Password-sharing
You can also give a passkey to someone you trust so you can both access shared accounts more safely, like an online grocery store. AirDrop requires proximity. Currently, passkeys may only be shared one by one.